Securing Web Applications with AWS ALB Authentication and OKTA OIDC
 Contents
Contents
- Introduction
- Assumptions
- Configuring OKTA
- Configuring AWS Application Load Balancer
- Shortcomings
- Resources
Introduction
AWS Elastic Load Balancer Service has introduced Builtin Authentication which supports any third party OIDC (Open ID Connect) Identity provider or AWS Cognito.
Many organizations use centralized identity servers like OKTA, Azure Active Directory, Auth0, and Onelogin to secure there complete cloud solutions.
Now with this support we can use same OIDC identity providers with less effort to provide Authentication to Web Apps and Web Pages which are behind the AWS ALB (Applcation Loadbalancer). It also helps to take off the load of authentication of users form web application. In this article i will be showing how we can use AWS ALB builtin authentication with OKTA OIDC.
Assumptions
OKTA Organization URL → https://dev-267174.okta.com
ALB Endpoint → https://www.alb-okta-test.com
Architecture
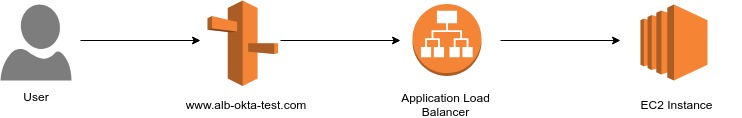
Configuring OKTA
Create a new OKTA Developer Account. We will be creating a new Client Application from Applications → Add Applications. Select the Application Platform as WEB
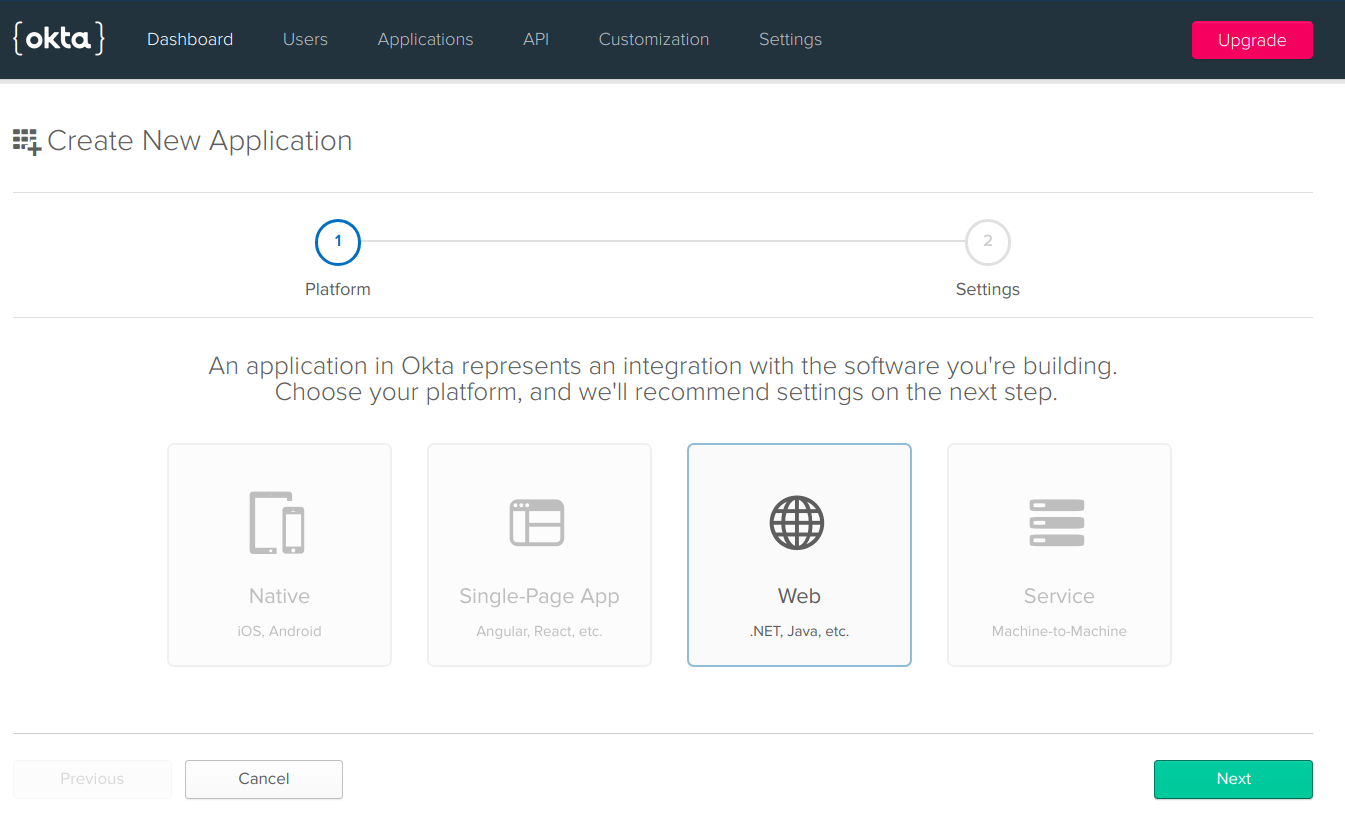
Give Application label → Any Name
Login redirect URIs → https://www.alb-okta-test.com/oauth2/idpresponse
Initiate login URI → https://www.alb-okta-test.com
Group assignments → Everyone or Any Specific Group
Grant type allowed → Authorization Code only
Once Created Note down the Client Credentials → Client ID & Client Secret
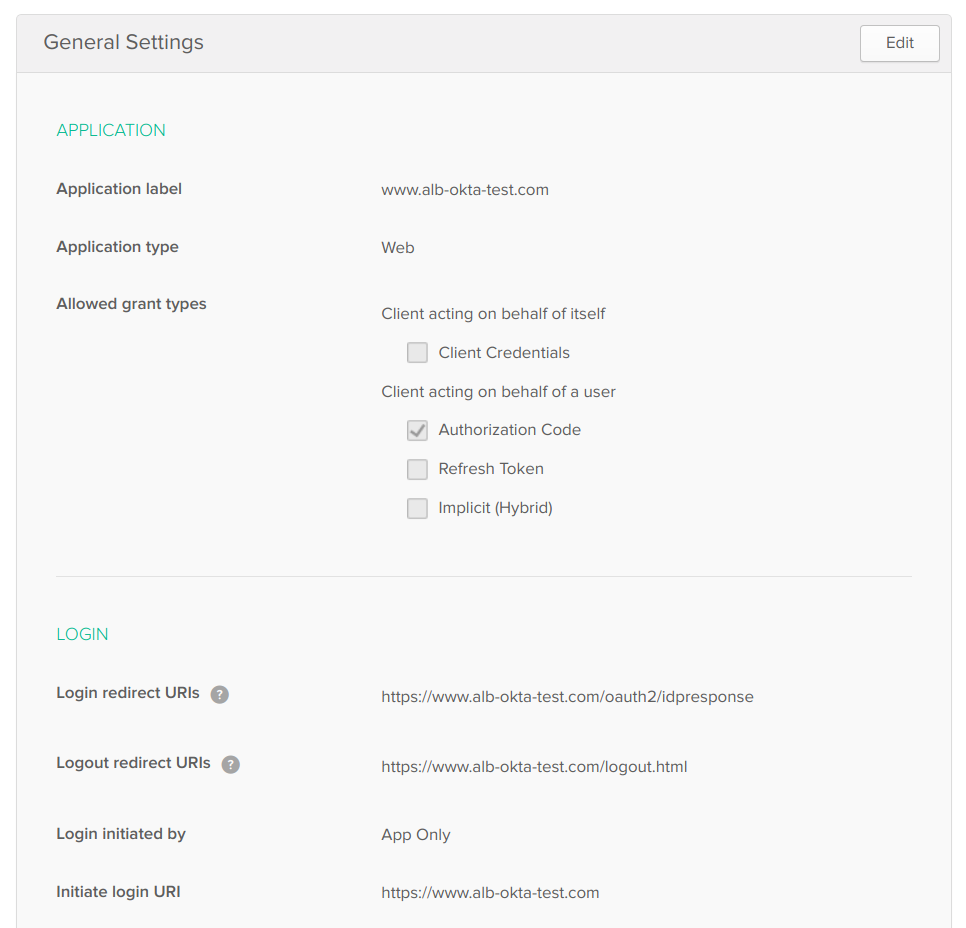 And in Assignments make sure you have atleast one User assigned to login.
And in Assignments make sure you have atleast one User assigned to login.
Goto API → Authorization Servers, Get your Issuer URI from there.
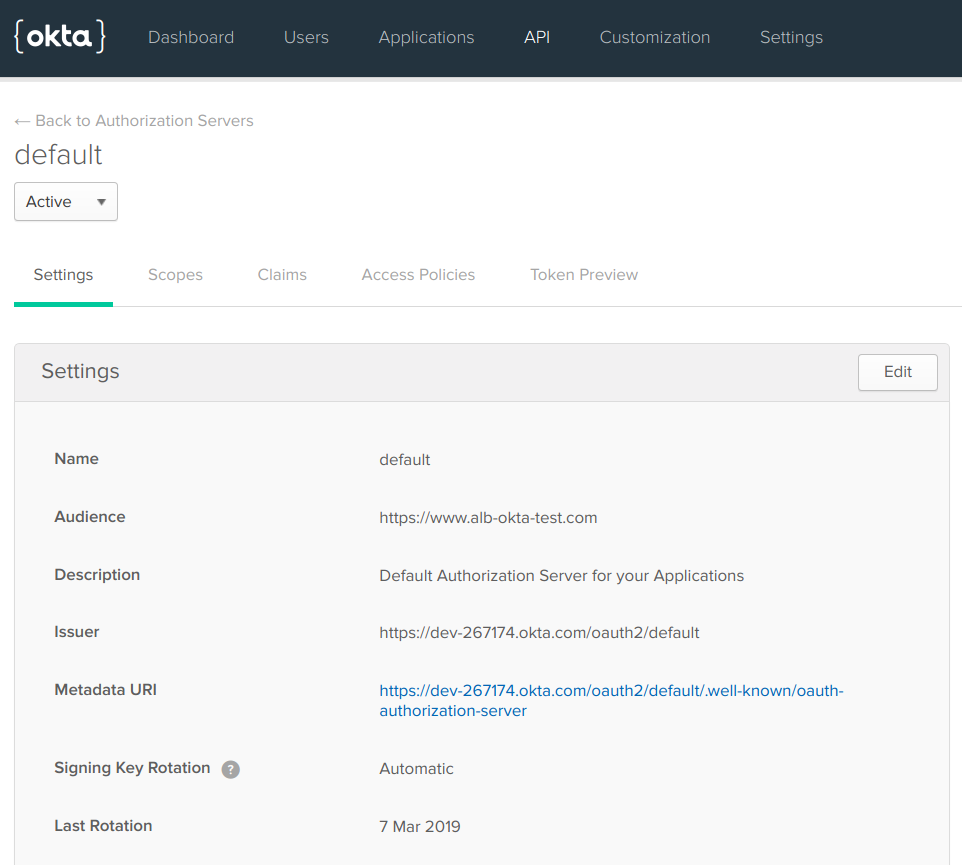
Now all your Endpoints will be
Issuer Endpoint → https://dev-267174.okta.com/oauth2/default
Authorization Endpoint → https://dev-267174.okta.com/oauth2/default/v1/authorize
Token Endpoint → https://dev-267174.okta.com/oauth2/default/v1/token
User Info Endpoint → https://dev-267174.okta.com/oauth2/default/v1/userinfo
Client ID & Client Secret → Get from the OKTA Client Application.
Configuring AWS Application Load Balancer
Assuming that Load Balancers, Target Groups and EC2 Instances have properly configured. Goto Amazon EC2 → Load Balancers → Select required ALB → Click on Listeners TAB → Select HTTPS → Click on Edit. You will be Redirected to Listener Pages
 Click on Add Action → Select Authenticate.
Click on Add Action → Select Authenticate.
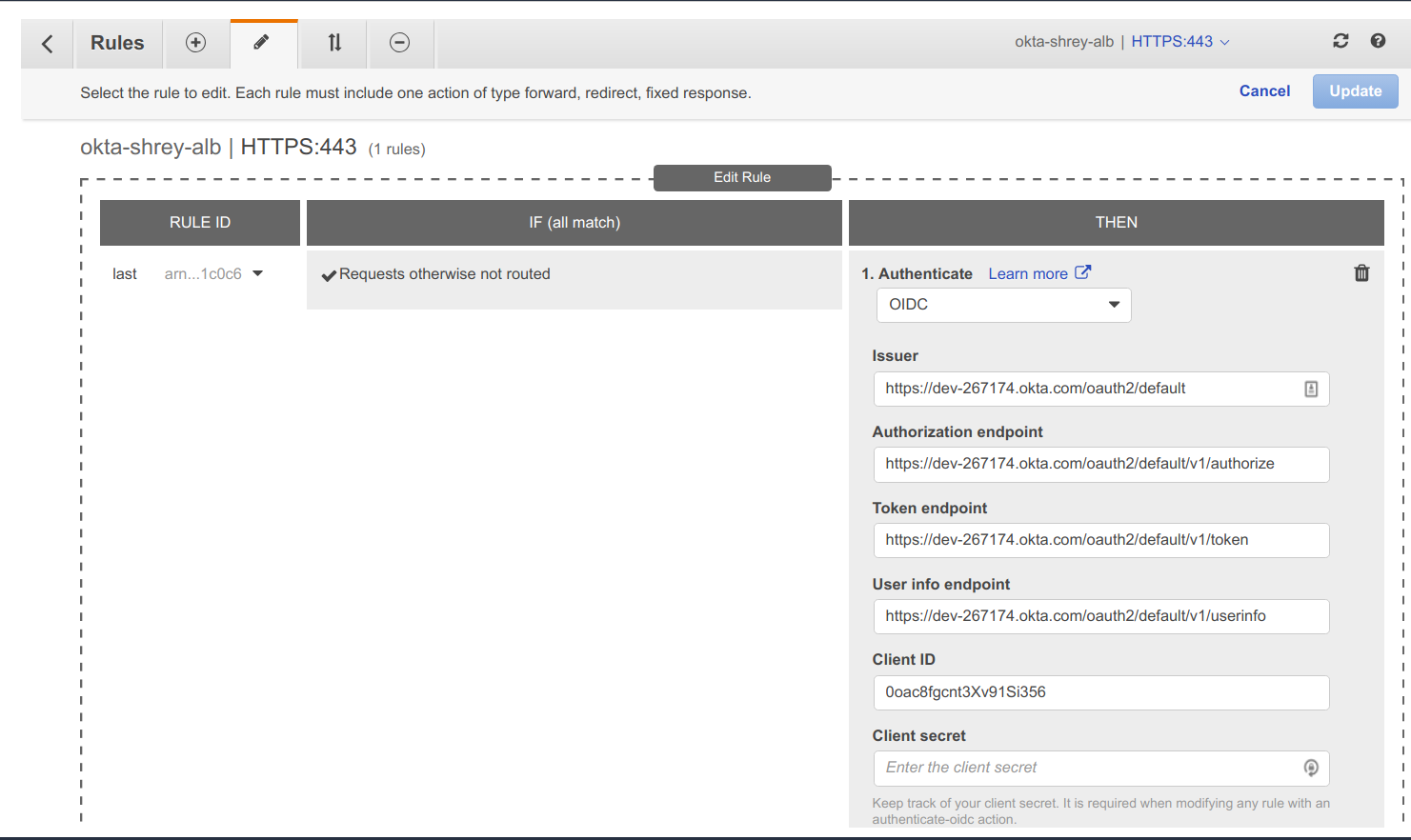
Under Authenticate
Authenticate → OIDC
Issuer Endpoint → https://dev-267174.okta.com/oauth2/default
Authorization Endpoint → https://dev-267174.okta.com/oauth2/default/v1/authorize
Token Endpoint → https://dev-267174.okta.com/oauth2/default/v1/token
User Info Endpoint → https://dev-267174.okta.com/oauth2/default/v1/userinfo
Client ID & Client Secret → Get it from your OKTA Client Application.
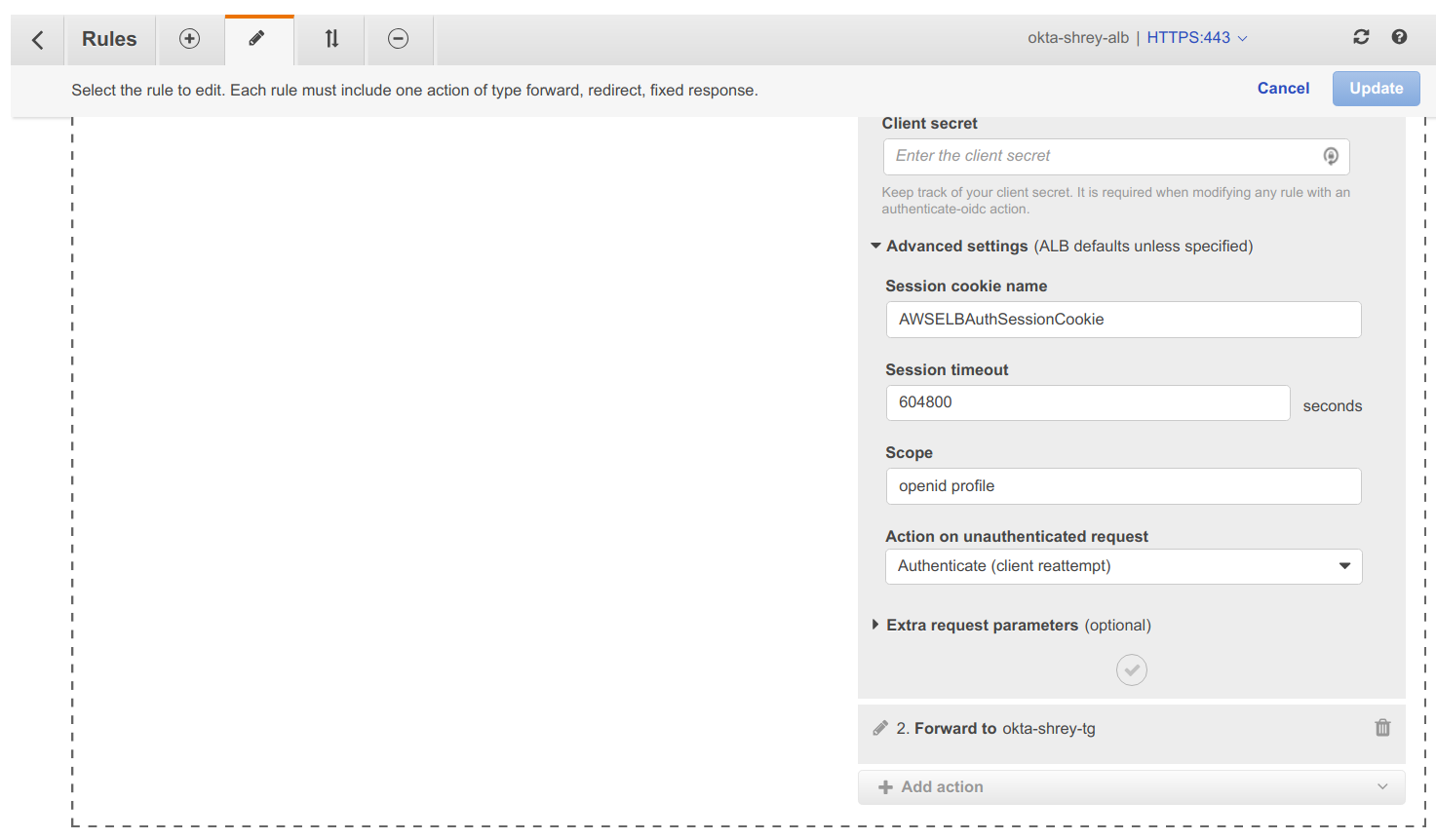
 Under Advanced Settings
Under Advanced Settings
Session cookie name → AWSELBAuthSessionCookie
Session timeout → 300
Scope → openid profile
Action on unauthenticated request → Authenticate (client reattempt)
 Now Click Save or Update. Visit
Now Click Save or Update. Visit https://www.alb-okta-test.com or your Load Balancer URL which will be redirected to OKTA Sign in Page
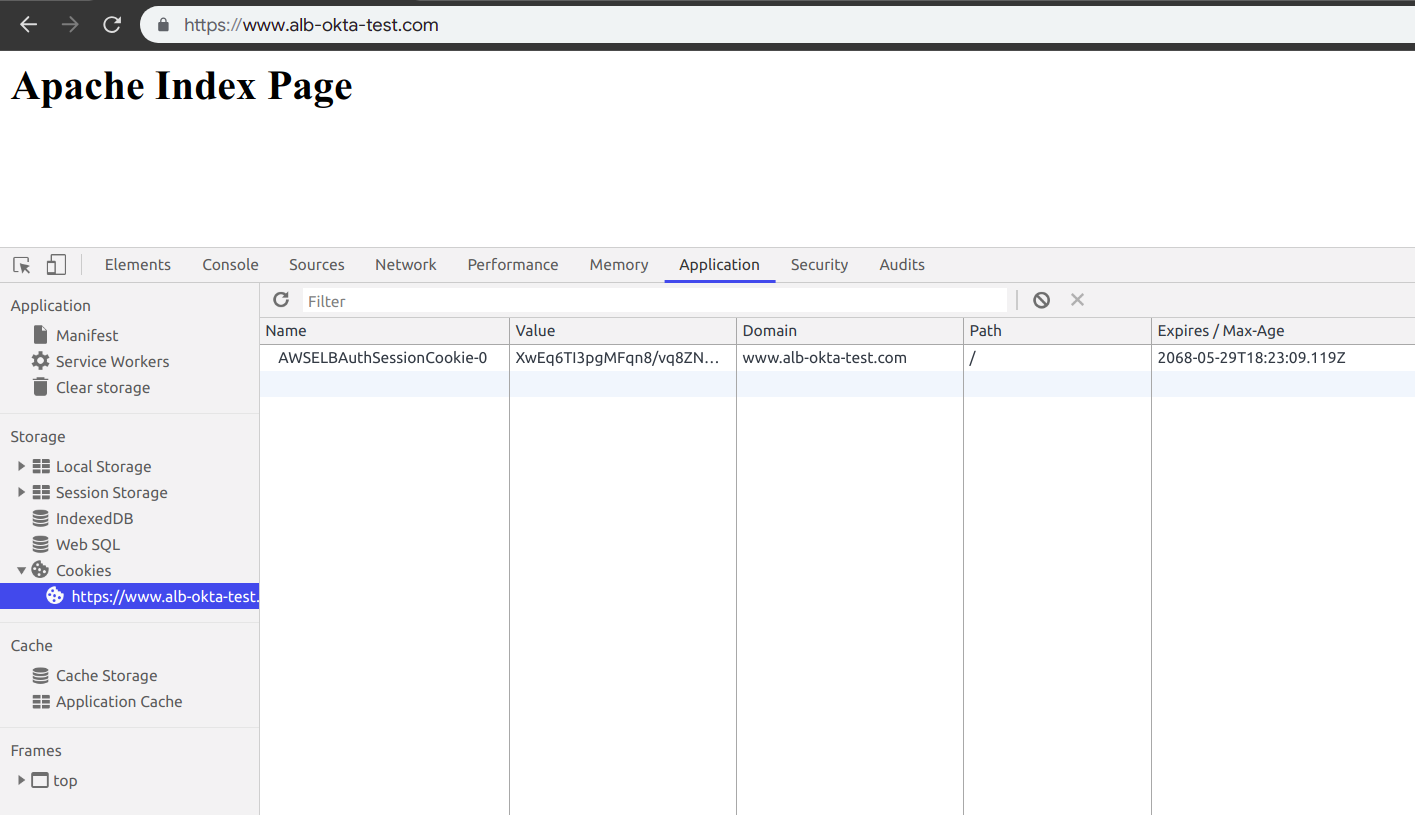
 Once Logged in You will able to view the site and AWS ALB Session Cookie is Set.
Once Logged in You will able to view the site and AWS ALB Session Cookie is Set.
Shortcomings
When an application needs to log out an authenticated user, it should set the expiration time of the authentication session cookie (AWSELBAuthSessionCookie) to -1 and redirect the client to the IdP (OKTA ) logout endpoint which is
GET https://dev-267174.okta.com/oauth2/default/v1/logout?id_token_hint=${id_token}
Since we do not have the id_token to make this request because the id_token was give to AWS ALB, we cannot see this in browser also, AWS ALB internally gets the id_token and sets the session cookie. One way to overcome this is set short session timeout like 300 seconds in loadbalancer configuration. Refer here